Provides a valid CompTIA Security+ sy0-501 exam dumps | 100% Free
Fulldumps shares online exam exercise questions all year round! CompTIA Security+ sy0-501 exam “CompTIASecurity+ Certification Exam” https://www.leads4pass.com/sy0-501.html (600 Q&As). Continue to study and we provide an updated cisco sy0-501 exam practice questions and answers. You can practice the test online!
Watch the CompTIA Security+ sy0-501 video tutorial online
Table of Contents:
- Latest CompTIA Security+ sy0-501 pdf
- Test your CompTIA Security+ sy0-501 exam level
- Related sy0-501 Popular Exam resources
- Get leads4pass Coupons (12% OFF)
- What are the advantages of leads4pass?
Latest CompTIA Security+ sy0-501 pdf
[PDF] Free CompTIA Security+ sy0-501 pdf dumps download from Google Drive: https://drive.google.com/open?id=1p48tIE7GSKFz_V895mWkWk7kaYHYEx0O
CompTIASecurity+ Certification – CompTIA IT Certifications: https://certification.comptia.org/certifications/security
Why is it different?
- No other certification that assesses baseline cybersecurity skills has performance-based questions on the exam. Security+ emphasizes hands-on practical skills, ensuring the security professional is better prepared to problem solve a wider variety of issues.
- More choose Security+ for DoD 8570 compliance than any other certification.
- Security+ focuses on the latest trends and techniques in risk management, risk mitigation, threat management, and intrusion detection.
- The new Security+ certification covers the Junior IT Auditor/Penetration Tester job role, in addition to the previous job roles for Systems Administrator, Network Administrator, and Security Administrator.
About the exam
CompTIA Security+ is the first security certification IT professionals should earn. It establishes the core knowledge required of any cybersecurity role and provides a springboard to intermediate-level cybersecurity jobs. Security+ incorporates best practices in hands-on trouble-shooting to ensure security professionals have practical security problem-solving skills. Cybersecurity professionals with Security+ know how to address security incidents – not just identify them.
The CompTIA Security+ exam will certify the successful candidate has the knowledge and skills required to install and configure systems to secure applications, networks, and devices; perform threat analysis and respond with appropriate mitigation techniques; participate in risk mitigation activities; and operate with an awareness of applicable policies, laws, and regulations. The successful candidate will perform these tasks to support the principles of confidentiality, integrity, and availability.
CompTIA Security+ sy0-501 Exam Practice Questions
QUESTION 1
A member of the admins group reports being unable to modify the “changes” file on a server. The permissions on the
file are as follows:
Permissions User Group File -rwxrw-r–+ Admins Admins changes
Based on the output above, which of the following BEST explains why the user is unable to modify the “changes” file?
A. The SELinux mode on the server is set to “enforcing.”
B. The SELinux mode on the server is set to “permissive.”
C. An FACL has been added to the permissions for the file.
D. The admins group does not have adequate permissions to access the file.
Correct Answer: C
QUESTION 2
A new firewall has been places into service at an organization. However, a configuration has not been entered on the
firewall. Employees on the network segment covered by the new firewall report they are unable to access the network.
Which of the following steps should be completed to BEST resolve the issue?
A. The firewall should be configured to prevent user traffic form matching the implicit deny rule.
B. The firewall should be configured with access lists to allow inbound and outbound traffic.
C. The firewall should be configured with port security to allow traffic.
D. The firewall should be configured to include an explicit deny rule.
Correct Answer: A
QUESTION 3
A company researched the root cause of a recent vulnerability in its software. It was determined that the vulnerability
was the result of two updates made in the last release. Each update alone would not have resulted in the vulnerability.
In order to prevent similar situations in the future, the company should improve which of the following?
A. Change management procedures
B. Job rotation policies
C. Incident response management
D. Least privilege access controls
Correct Answer: A
QUESTION 4
A user suspects someone has been accessing a home network without permission by spoofing the MAC address of an
authorized system. While attempting to determine if an authorized user is logged into the home network, the user
reviews the wireless router, which shows the following table for systems that are currently on the home network.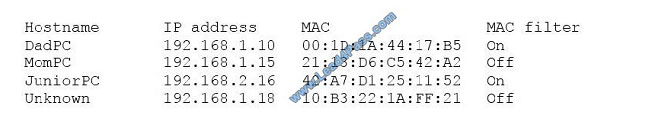
Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
A. Apply MAC filtering and see if the router drops any of the systems.
B. Physically check each of the authorized systems to determine if they are logged onto the network.
C. Deny the “unknown” host because the hostname is not known and MAC filtering is not applied to this host.
D. Conduct a ping sweep of each of the authorized systems and see if an echo response is received.
Correct Answer: C
QUESTION 5
A technician needs to implement a system which will properly authenticate users by their username and password only
when the users are logging in from a computer in the office building. Any attempt to authenticate from a location other
than the office building should be rejected.
Which of the following MUST the technician implement?
A. Dual factor authentication
B. Transitive authentication
C. Single factor authentication
D. Biometric authentication
Correct Answer: B
QUESTION 6
For each of the given items, select the appropriate authentication category from the drop down choices.
Select the appropriate authentication type for the following items:
Hot Area:
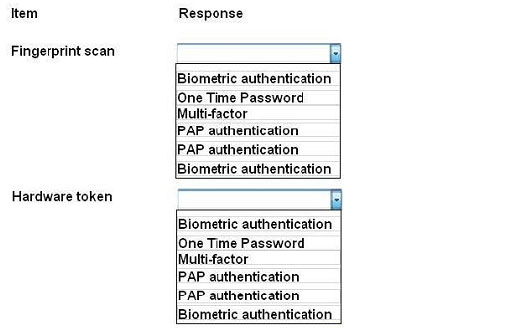
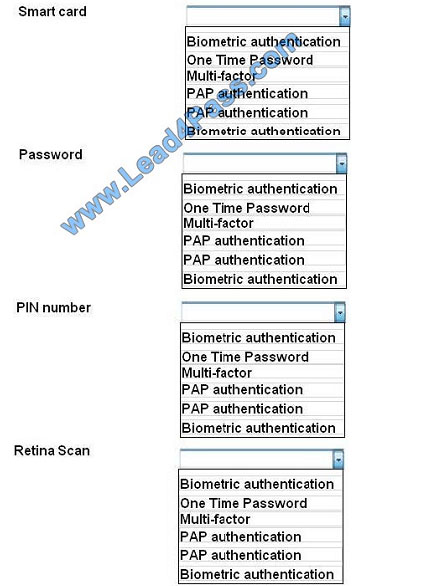
Correct Answer:
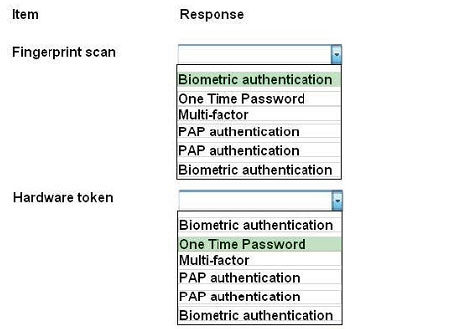
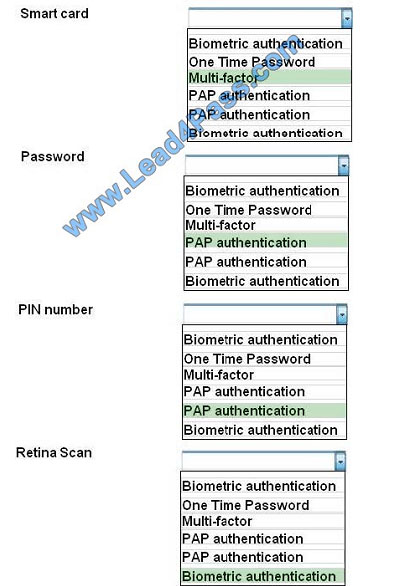
Biometrics refers to a collection of physical attributes of the human body that can be used as identification or an
authentication factor. Fingerprints and retinas are physical attributes of the human body.
Two types of tokens exist, Time-based one-time password (TOTP) tokens and HMACbased one-time password
(HOTP). TOTP tokens generate passwords at fixed time intervals, whereas HOTP tokens generate passwords not
based on fixed
time intervals but instead based on a non-repeating one-way function, such as a hash or HMAC operation.
Smart cards can have Multi-factor and proximity authentication embedded into it.
PAP allows for two entities to share a password in advance and use the password as the basis of authentication. The
same goes for PIN numbers.
References:
Stewart, James Michael, CompTIA Security+ Review Guide, Sybex, Indianapolis, 2014, pp. 282, 285
http://en.wikipedia.org/wiki/Password_authentication_protocol#Working_cycle
http://en.wikipedia.org/wiki/Smart_card#Security
QUESTION 7
An organization requires users to provide their fingerprints to access an application. To improve security, the application
developers intend to implement multifactor authentication. Which of the following should be implemented?
A. Use a camera for facial recognition
B. Have users sign their name naturally
C. Require a palm geometry scan
D. Implement iris recognition
Correct Answer: B
QUESTION 8
An attacker uses a network sniffer to capture the packets of a transaction that adds $20 to a gift card. The attacker then
user a function of the sniffer to push those packets back onto the network again, adding another $20 to the gift card.
This can be done many times.
Which of the following describes this type of attack?
A. Integer overflow attack
B. Smurf attack
C. Replay attack
D. Buffer overflow attack
E. Cross-site scripting attack
Correct Answer: C
QUESTION 9
The help desk is receiving numerous password change alerts from users in the accounting department. These alerts
occur multiple times on the same day for each of the affected users\\’ accounts.
Which of the following controls should be implemented to curtail this activity?
A. Password Reuse
B. Password complexity
C. Password History
D. Password Minimum age
Correct Answer: D
QUESTION 10
Which of the following attacks allows access to contact lists on cellular phones?
A. War chalking
B. Blue jacking
C. Packet sniffing
D. Bluesnarfing
Correct Answer: D
QUESTION 11
An external auditor visits the human resources department and performs a physical security assessment. The auditor
observed documents on printers that are unclaimed. A closer look at these documents reveals employee names,
addresses, ages, and types of medical and dental coverage options each employee has selected.
Which of the following is the MOST appropriate actions to take?
A. Flip the documents face down so no one knows these documents are PII sensitive
B. Shred the documents and let the owner print the new set
C. Retrieve the documents, label them with a PII cover sheet, and return them to the printer
D. Report to the human resources manager that their personnel are violating a privacy policy
Correct Answer: D
QUESTION 12
A security analyst wishes to increase the security of an FTP server. Currently, all traffic to the FTP server is
unencrypted. Users connecting to the FTP server use a variety of modern FTP client software. The security analyst
wants to keep the same port and protocol, while also still allowing unencrypted connections. Which of the following
would BEST accomplish these goals?
A. Require the SFTP protocol to connect to the file server.
B. Use implicit TLS on the FTP server.
C. Use explicit FTPS for connections.
D. Use SSH tunneling to encrypt the FTP traffic.
Correct Answer: C
QUESTION 13
Which of the following allows an application to securely authenticate a user by receiving credentials from a web
domain?
A. TACACS+
B. RADIUS
C. Kerberos
D. SAML
Correct Answer: D
Related sy0-501 Popular Exam resources
| title | youtube | CompTIA | leads4pass | leads4pass Total Questions | |
|---|---|---|---|---|---|
| CompTIA Security+ | leads4pass sy0-501 dumps pdf | leads4pass sy0-501 youtube | CompTIA Security+ Certification – CompTIA IT Certifications | https://www.leads4pass.com/sy0-501.html | 600 Q&A |
Get leads4pass Coupons(12% OFF)

What are the advantages of leads4pass?
We have a number of CompTIA, CompTIA, IBM, CompTIA, and other exam experts. We update exam data throughout the year.
Top exam pass rate! We have a large user base. We are an industry leader! Choose leads4pass to pass the exam with ease!

Summarize:
The free CompTIA Security+ sy0-501 exam dumps can help you improve your skills and exam experience! To pass the cisco sy0-501 exam at once: https://www.leads4pass.com/sy0-501.html We make CompTIA sy0-501 videos and sy0-501 pdf for you to learn! I hope you can pass the exam easily.
Discover more from Collect the latest Microsoft (Azure, Dynamics 365, Microsoft 365, Fundamentals, MTA...) exam questions and answers-Advanced sharing with Cisco, CompTIA, Citrix
Subscribe to get the latest posts sent to your email.

