Microsoft SC-100 dumps the latest effective exam solution

Microsoft SC-100 dumps are the latest and most effective exam solution to aid candidates in their pre-exam practice!
Microsoft SC-100 dumps have been updated! Reviewed, corrected, and actually verified by the Microsoft team, it is true and effective! Meet the conditions for successfully passing the Microsoft Cybersecurity Architect Expert certification exam.
Microsoft SC-100 dumps contain 180 latest exam questions and answers, which truly cover all Microsoft Cybersecurity Architect Expert exam requirements.
New Microsoft SC-100 dumps details:
| Total Questions: | 180 |
| Single & Multiple Choice: | 133 |
| Drag Drop: | 6 |
| Hotspot: | 41 |
| Testlet: | 2 |
Use the latest and most effective Microsoft SC-100 certification exam solution: Download Microsoft SC-100 dumps with PDF and VCE: https://www.leads4pass.com/sc-100.html to help you study easily and successfully pass the Microsoft Cybersecurity Architect Expert certification exam.
Share some New Microsoft SC-100 dumps exam questions online practice for free:
| From | Number of exam questions | Associated certification |
| leads4pass | 15 | Fundamental, Role-based |
New Question 1:
After you answer a question in this section, you cannot return to it. As a result, these questions will not appear in the review screen.
You are designing the encryption standards for data at rest for an Azure resource.
You need to provide recommendations to ensure that the data at rest is encrypted by using AES-256 keys. The solution must support rotating the encryption keys monthly.
Solution: For blob containers in Azure Storage, you recommend encryption that uses Microsoft-managed keys within an encryption scope.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Need to use customer-managed keys instead.
Note: Automated key rotation in Key Vault allows users to configure Key Vault to generate a new key version at a specified frequency automatically. You can use a rotation policy to configure rotation for each key. Our recommendation is to rotate encryption keys at least every two years to meet cryptographic best practices. This feature enables end-to-end zero-touch rotation for encryption at rest for Azure services with a customer-managed key (CMK) stored in Azure Key Vault. Please refer to specific Azure service documentation to see if the service covers the end
to-end rotation.
Reference: https://docs.microsoft.com/en-us/azure/key-vault/keys/how-to-configure-key-rotation
New Question 2:
After you answer a question in this section, you cannot return to it. As a result, these questions will not appear in the review screen.
Your on-premises network contains an e-commerce web app developed in Angular and Node, js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
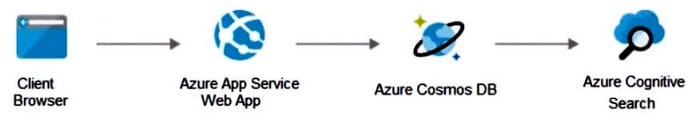
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend implementing Azure Front Door with Azure Web Application Firewall (WAF).
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Instead, use the solution: You recommend creating private endpoints for the web app and the database layer.
Note:
How to Use Azure Private Endpoints to Restrict Public Access to WebApps.
As an Azure administrator or architect, you are sometimes asked the question: “How can we safely deploy internal business applications to Azure App Services?”
These applications characteristically are:
Not accessible from the public internet.
Accessible from within the on-premises corporate network
Accessible via an authorized VPN client from outside the corporate network.
For such scenarios, we can use Azure Private Links, which enables private and secure access to Azure PaaS services over Azure Private Endpoints, along with the Site-to-Site VPN, Point-to-Site VPN, or the Express Route.
Azure Private Endpoint is a read-only network interface service associated with the Azure PAAS Services. It allows you to bring deployed sites into your virtual network, limiting access to them at the network level.
It uses one of the private IP addresses from your Azure VNet and associates it with the Azure App Services. These services are called Private Link resources. They can be Azure Storage, Azure Cosmos DB, SQL, App Services Web App, your own / partner-owned services, Azure Backups, Event Grids, Azure Service Bus, or Azure Automation.
Reference: https://www.varonis.com/blog/securing-access-azure-webapps
New Question 3:
You are creating an application lifecycle management process based on the Microsoft Security Development Lifecycle (SDL).
You need to recommend a security standard for onboarding applications to Azure. The standard will include recommendations for application design, development, and deployment
What should you include during the application design phase?
A. static application security testing (SAST) by using SonarQube
B. dynamic application security testing (DAST) by using Veracode
C. threat modeling by using the Microsoft Threat Modeling Tool
D. software decomposition by using Microsoft Visual Studio Enterprise
Correct Answer: C
Threat modeling is a core element of the Microsoft Security Development Lifecycle (SDL). It\’s an engineering technique you can use to help you identify threats, attacks, vulnerabilities, and countermeasures that could affect your application.
You can use threat modeling to shape your application\’s design, meet your company\’s security objectives, and reduce risk.
Incorrect:
Not B: Advantages of Veracode\’s DAST test solution
With a Blackbox test tool from Veracode, you can:
Simulate the actions of an actual attacker to discover vulnerabilities not found by other testing techniques.
Run tests on applications developed in any language – JAVA/JSP, PHP, and other engine-driven web applications.
Provide development and QA teams with a report on critical vulnerabilities along with information that lets them recreate the flaws.
Fix issues more quickly with detailed remediation information.
Develop long-term strategies for improving application security across your software portfolio using guidance and proactive recommendations from Veracode\’s expert.
Not D: SonarQube is a leading automatic code review tool to detect bugs, vulnerabilities, and code smells in your code. Using Static Application Security Testing (SAST) you can do an analysis of vulnerabilities in your code, also known as white-box testing to find about 50% of likely issues.
Reference: https://www.microsoft.com/en-us/securityengineering/sdl/threatmodeling
New Question 4:
Your company is moving a big data solution to Azure.
The company plans to use the following storage workloads:
1.
Azure Storage blob containers
2.
Azure Data Lake Storage Gen2
3.
Azure Storage file shares
4.
Azure Disk Storage
Which two storage workloads support authentication by using Azure AD? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Azure Storage file shares
B. Azure Disk Storage
C. Azure Storage blob containers
D. Azure Data Lake Storage Gen2
Correct Answer: CD
C: Azure Storage supports using Azure Active Directory (Azure AD) to authorize requests to blob data. With Azure AD, you can use Azure role-based access control (Azure RBAC) to grant permissions to a security principal, which may be a user, group, or application service principal. The security principal is authenticated by Azure AD to return an OAuth 2.0 token. The token can then be used to authorize a request against the Blob service.
You can scope access to Azure blob resources at the following levels, beginning with the narrowest scope:
*
An individual container. At this scope, a role assignment applies to all of the blobs in the container, as well as container properties and metadata.
*
The storage account.
*
The resource group.
*
The subscription.
*
A management group.
D: You can securely access data in an Azure Data Lake Storage Gen2 (ADLS Gen2) account using OAuth 2.0 with an Azure Active Directory (Azure AD) application service principal for authentication. Using a service principal for authentication provides two options for accessing data in your storage account:
A mount point to a specific file or path
Direct access to data
Incorrect:
Not A: To enable AD DS authentication over SMB for Azure file shares, you need to register your storage account with AD DS and then set the required domain properties on the storage account.
To register your storage account with AD DS, create an account representing it in your AD DS.
Reference: https://docs.microsoft.com/en-us/azure/storage/blobs/authorize-access-azure-active-directory https://docs.microsoft.com/en-us/azure/databricks/data/data-sources/azure/adls-gen2/azure-datalake-gen2-sp-access
New Question 5:
Your company plans to deploy several Azure App Service web apps. The web apps will be deployed to the West Europe Azure region. The web apps will be accessed only by customers in Europe and the United States.
You need to recommend a solution to prevent malicious bots from scanning the web apps for vulnerabilities. The solution must minimize the attached surface.
What should you include in the recommendation?
A. Azure Firewall Premium
B. Azure Traffic Manager and application security groups
C. Azure Application Gateway Web Application Firewall (WAF)
D. network security groups (NSGs)
Correct Answer: B
*
Application security groups enable you to configure network security as a natural extension of an application\’s structure, allowing you to group virtual machines and define network security policies based on those groups.
You can reuse your security policy at scale without manual maintenance of explicit IP addresses. The platform handles the complexity of explicit IP addresses and multiple rule sets, allowing you to focus on your business logic.
*
Azure Traffic Manager is a DNS-based traffic load balancer. This service allows you to distribute traffic to your public-facing applications across the global Azure regions. Traffic Manager also provides your public endpoints with high availability and quick responsiveness.
Traffic Manager uses DNS to direct the client requests to the appropriate service endpoint based on a traffic-routing method. The traffic manager also provides health monitoring for every endpoint.
Incorrect:
Not C: Azure Application Gateway Web Application Firewall is too small a scale solution in this scenario.
Note: Attacks against a web application can be monitored by using a real-time Application Gateway that has a Web Application Firewall, enabled with integrated logging from Azure Monitor to track Web Application Firewall alerts and easily monitor trends.
Reference: https://docs.microsoft.com/en-us/azure/virtual-network/application-security-groups https://docs.microsoft.com/en-us/azure/traffic-manager/traffic-manager-overview https://docs.microsoft.com/en-us/security/benchmark/azure/baselines/app-service-security-baseline
New Question 6:
Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription. The company uses the following devices:
1.
Computers that run either Windows 10 or Windows 11
2.
Tablets and phones that run either Android or iOS
You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored.
What should you include in the recommendation?
A. eDiscovery
B. Microsoft Information Protection
C. Compliance Manager
D. retention policies
Correct Answer: B
Protect your sensitive data with Microsoft Purview.
Implement capabilities from Microsoft Purview Information Protection (formerly Microsoft Information Protection) to help you discover, classify, and protect sensitive information wherever it lives or travels.
Note: You can use Microsoft Information Protection: Microsoft Purview for Auditing and Analytics in Outlook for iOS, Android, and Mac (DoD).
Incorrect:
Not A: Electronic discovery, or eDiscovery, is the process of identifying and delivering electronic information that can be used as evidence in legal cases. You can use eDiscovery tools in Microsoft Purview to search for content in Exchange Online, OneDrive for Business, SharePoint Online, Microsoft Teams, Microsoft 365 Groups, and Yammer Teams.
You can search mailboxes and sites in the same eDiscovery search, and then export the search results. You can use Microsoft Purview eDiscovery (Standard) cases to identify, hold, and export content found in mailboxes and sites.
If your organization has an Office 365 E5 or Microsoft 365 E5 subscription (or related E5 add-on subscriptions), you can further manage custodians and analyze content by using the feature-rich Microsoft Purview eDiscovery (Premium) solution in Microsoft 365.
Not C: What does the compliance Manager do?
Compliance managers ensure that a business, its employees, and its projects comply with all relevant regulations and specifications. This could include health and safety, environmental, legal, or quality standards, as well as any ethical policies the company may have.
Not D: A retention policy (also called a \’ schedule\’) is a key part of the lifecycle of a record. It describes how long a business needs to keep a piece of information (a record), where it is stored, and how to dispose of the record when it is time.
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection
https://docs.microsoft.com/en-us/microsoft-365/compliance/ediscovery?view=o365-worldwide
New Question 7:
For a Microsoft cloud environment, you are designing a security architecture based on the Microsoft Cloud Security Benchmark.
What are the three best practices for identity management based on the Azure Security Benchmark? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Manage application identities securely and automatically.
B. Manage the lifecycle of identities and entitlements
C. Protect identity and authentication systems.
D. Enable threat detection for identity and access management.
E. Use a centralized identity and authentication system.
Correct Answer: ACE
New Question 8:
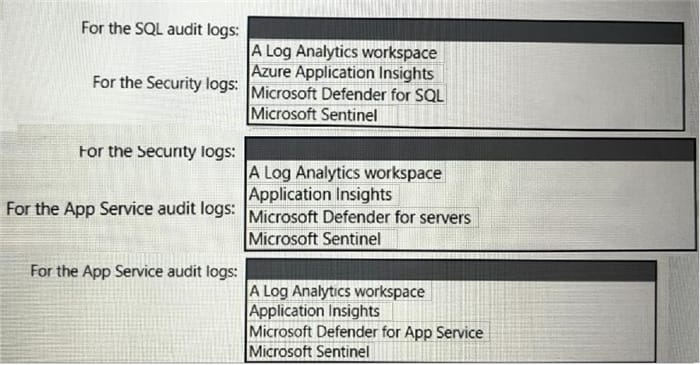
You are designing an auditing solution for Azure landing zones that will contain the following components:
1.
SQL audit logs for Azure SQL databases
2.
Windows Security logs from Azure virtual machines
3.
Azure App Service audit logs from App Service web apps
You need to recommend a centralized logging solution for the landing zones. The solution must meet the following requirements:
Log all privileged access.
Retain logs for at least 365 days.
Minimize costs.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Hot Area:
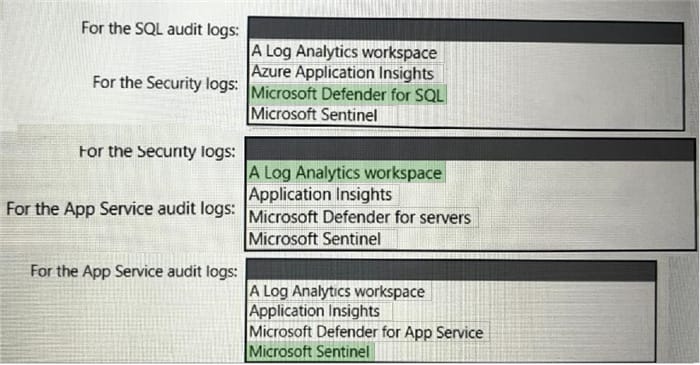
Correct Answer:
New Question 9:
Your company plans to provision blob storage by using an Azure Storage account. The blob storage will be accessible from 20 application servers on the internet.
You need to recommend a solution to ensure that only the application servers can access the storage account.
What should you recommend using to secure the blob storage?
A. managed rule sets in Azure Web Application Firewall (WAF) policies
B. inbound rules in network security groups (NSGs)
C. firewall rules for the storage account
D. inbound rules in Azure Firewall
E. service tags in network security groups (NSGs)
Correct Answer: C
Configure Azure Storage firewalls and virtual networks.
To secure your storage account, you should first configure a rule to deny access to traffic from all networks (including internet traffic) on the public endpoint, by default. Then, you should configure rules that grant access to traffic from specific VNets.
You can also configure rules to grant access to traffic from selected public internet IP address ranges, enabling connections from specific internet or on-premises clients. This configuration enables you to build a secure network boundary for your applications.
Storage firewall rules apply to the public endpoint of a storage account. You don’t need any firewall access rules to allow traffic for private endpoints of a storage account. The process of approving the creation of a private endpoint grants implicit access to traffic from the subnet that hosts the private endpoint.
Incorrect:
Not B: You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network.
A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol.
Not E: A service tag represents a group of IP address prefixes from a given Azure service. Microsoft manages the address prefixes encompassed by the service tag and automatically updates the service tag as addresses change, minimizing the complexity of frequent updates to network security rules.
Reference: https://docs.microsoft.com/en-us/azure/storage/common/storage-network-security
New Question 10:
Your company has an on-premises network and an Azure subscription.
The company does NOT have a Site-to-Site VPN or an ExpressRoute connection to Azure.
You are designing the security standards for Azure App Service web apps. The web apps will access Microsoft SQL Server databases on the network.
You need to recommend security standards that will allow the web apps to access the databases. The solution must minimize the number of open internet-accessible endpoints to the on-premises network.
What should you include in the recommendation?
A. a private endpoint
B. hybrid connections
C. virtual network NAT gateway integration
D. virtual network integration
Correct Answer: B
Hybrid Connections can connect Azure App Service Web Apps to on-premises resources that use a static TCP port. Supported resources include Microsoft SQL Server, MySQL, HTTP Web APIs, Mobile Services, and most custom Web Services.
Note: You can use an Azure App Service Hybrid Connections. To do this, you need to add and create Hybrid Connections in your app. You will download and install an agent (the Hybrid Connection Manager) in the database server or another server that is in the same network as the on-premise database.
You configure a logical connection on your app service or web app.
A small agent, the Hybrid Connection Manager, is downloaded and installed on a Windows Server (2012 or later) running in the remote network (on-premises or anywhere) that you need to communicate with.
You log into your Azure subscription in the Hybrid Connection Manager and select the logical connection in your app service.
The Hybrid Connection Manager will initiate a secure tunnel out (TCP 80/443) to your app service in Azure.
Your app service can now communicate with TCP-based services, on Windows or Linux, in the remote network via the Hybrid Connection Manager.
You could get more details on how to Connect Azure Web Apps To On-Premises.
Incorrect:
Not A: NAT gateway provides outbound internet connectivity for one or more subnets of a virtual network. Once the NAT gateway is associated with a subnet, NAT provides source network address translation (SNAT) for that subnet. NAT gateway specifies which static IP addresses virtual machines use when creating outbound flows.
However, we need an inbound connection.
Not C: You can Azure web app service VNet integration with Azure VPN gateway to securely access the resource in an Azure VNet or on-premise network.
Note: Virtual network integration gives your app access to resources in your virtual network, but it doesn’t grant inbound private access to your app from the virtual network.
Private site access refers to making an app accessible only from a private network, such as from within an Azure virtual network. Virtual network integration is used only to make outbound calls from your app into your virtual network.
The virtual network integration feature behaves differently when it is used with virtual networks in the same region and with virtual networks in other regions. The virtual network integration feature has two variations:
Regional virtual network integration: When you connect to virtual networks in the same region, you must have a dedicated subnet in the virtual network you\’re integrating with.
Gateway-required virtual network integration: When you connect directly to virtual networks in other regions or to a classic virtual network in the same region, you need an Azure Virtual Network gateway created in the target virtual network.
New Question 11:
Your company has the virtual machine infrastructure shown in the following table.
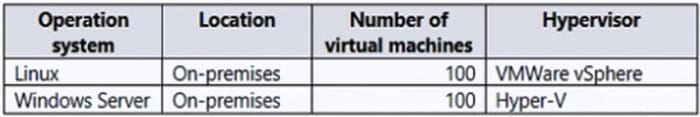
The company plans to use Microsoft Azure Backup Server (MABS) to back up the virtual machines to Azure.
You need to provide recommendations to increase the resiliency of the backup strategy to mitigate attacks such as ransomware.
What should you include in the recommendation?
A. Use geo-redundant storage (GRS).
B. Maintain multiple copies of the virtual machines.
C. Encrypt the backups by using customer-managed keys (CMKS).
D. Require PINs to disable backups.
Correct Answer: D
Azure Backup
Checks have been added to make sure only valid users can perform various operations. These include adding an extra layer of authentication. As part of adding an extra layer of authentication for critical operations, you\’re prompted to enter a security PIN before modifying online backups.
Authentication to perform critical operations
As part of adding an extra layer of authentication for critical operations, you\’re prompted to enter a security PIN when you perform Stop Protection with Delete data and Change Passphrase operations.
https://docs.microsoft.com/en-us/azure/backup/backup-azure-security-feature#prevent-attacks
New Question 12:
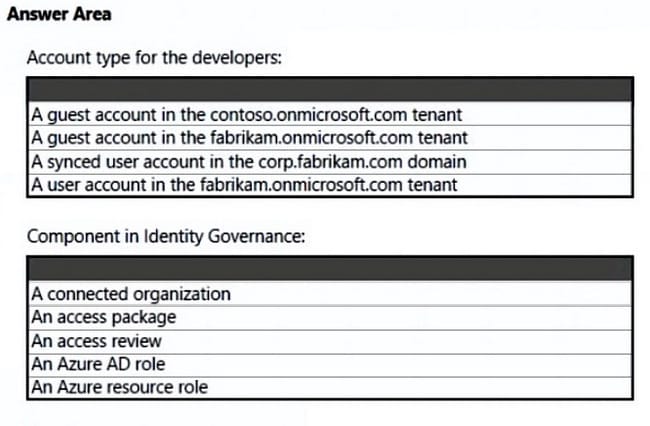
What should you create in Azure AD to meet the Contoso developer requirements?
Hot Area:
Correct Answer:
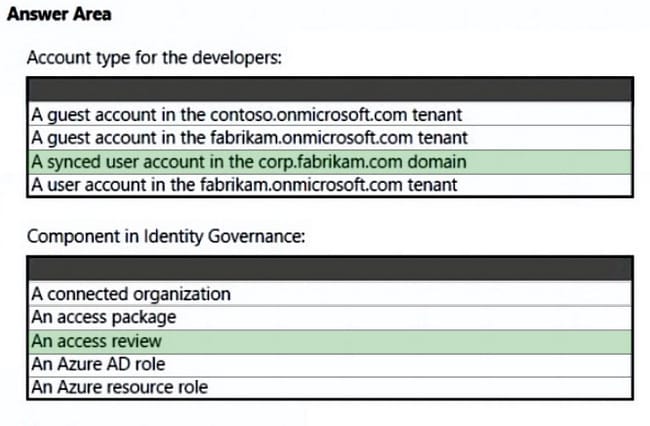
Box 1: A synced user account
Need to use a synched user account.
Incorrect:
*
Not A user account in the fabrikam.onmicrosoft.com tenant
The Contoso developers must use their existing contoso.onmicrosoft.com credentials to access the resources in Sub1.
*
Guest accounts would not meet the requirements.
Note: Developers at Contoso will connect to the resources of Fabrikam to test or update applications. The developers will be added to a security group named ContosoDevelopers in fabrikam.onmicrosoft.com that will be assigned to roles in Sub1.
The ContosoDevelopers group is assigned the db_owner role for the ClaimsDB database.
Contoso Developers Requirements
Fabrikam identifies the following requirements for the Contoso developers:
Every month, the membership of the ContosoDevelopers group must be verified.
The Contoso developers must use their existing contoso.onmicrosoft.com credentials to access the resources in Sub1.
The Contoso developers must be prevented from viewing the data in a column named MedicalHistory in the ClaimDetails table.
Box 2: An access review
Scenario: Every month, the membership of the ContosoDevelopers group must be verified.
Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. User\’s access can be reviewed on a regular basis to make sure only the right people have continued access.
Access review is part of Azure AD Identity governance.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory-domain-services/synchronization
https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
New Question 13:
HOTSPOT
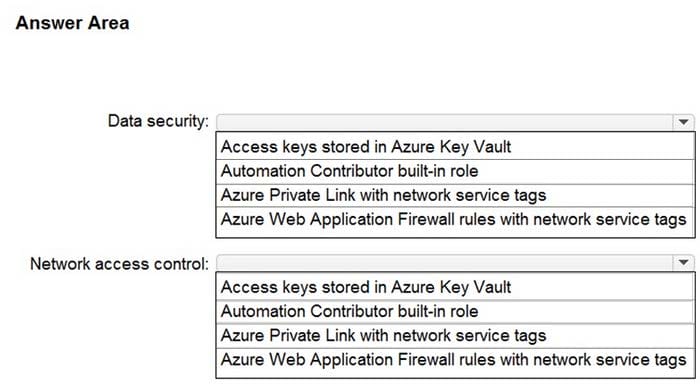
You are designing security for a runbook in an Azure Automation account. The runbook will copy data to Azure Data Lake Storage Gen2.
You need to recommend a solution to secure the components of the copy process.
What should you include in the recommendation for each component? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
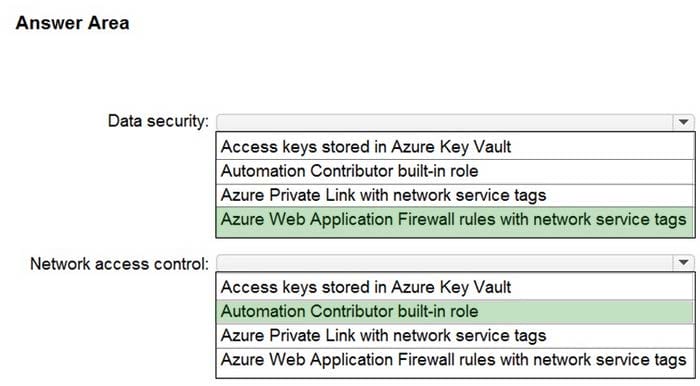
Box 1: Azure Web Application Firewall with network service tags A service tag represents a group of IP address prefixes from a given Azure service. Microsoft manages the address prefixes encompassed by the service tag and automatically updates the service tag as addresses change, minimizing the complexity of frequent updates to network security rules.
You can use service tags to define network access controls on network security groups, Azure Firewall, and user-defined routes.
Incorrect:
* Not Azure private link with network service tags Network service tags are not used with Private links.
Box 2: Automation Contributor built-in role
The Automation Contributor role allows you to manage all resources in the Automation account, except modifying other user\’s access permissions to an Automation account.
Reference: https://docs.microsoft.com/en-us/azure/virtual-network/service-tags-overview
https://docs.microsoft.com/en-us/azure/automation/automation-role-based-access-control
New Question 14:
A customer has a hybrid cloud infrastructure that contains a Microsoft 365 E5 subscription and an Azure subscription.
All on-premises servers in the perimeter network are prevented from connecting directly to the internet.
The customer recently recovered from a ransomware attack.
The customer plans to deploy Microsoft Sentinel.
You need to recommend solutions to meet the following requirements:
1.
Ensure that the security operations team can access the security logs and the operation logs.
2.
Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network. Which two solutions should you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. a custom collector that uses the Log Analytics agent
B. the Azure Monitor agent
C. resource-based role-based access control (RBAC)
D. Azure Active Directory (Azure AD) Conditional Access policies
Correct Answer: BC
A: You can collect data in custom log formats to Microsoft Sentinel with the Log Analytics agent.
Note: You can use the Log Analytics agent to collect data in text files of nonstandard formats from both Windows and Linux computers. Once collected, you can either parse the data into individual fields in your queries or extract the data during collection to individual fields.
You can connect your data sources to Microsoft Sentinel using custom log formats.
C: Microsoft Sentinel uses Azure role-based access control (Azure RBAC) to provide built-in roles that can be assigned to users, groups, and services in Azure.
Use Azure RBAC to create and assign roles within your security operations team to grant appropriate access to Microsoft Sentinel. The different roles give you fine-grained control over what Microsoft Sentinel users can see and do.
Azure roles can be assigned in the Microsoft Sentinel workspace directly (see note below), or in a subscription or resource group that the workspace belongs to, which Microsoft Sentinel inherits.
Incorrect:
A: You can collect data in custom log formats to Microsoft Sentinel with the Log Analytics agent.
Note: You can use the Log Analytics agent to collect data in text files of nonstandard formats from both Windows and Linux computers. Once collected, you can either parse the data into individual fields in your queries or extract the data during collection to individual fields.
You can connect your data sources to Microsoft Sentinel using custom log formats.
Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/agents/agents-overview https://docs.microsoft.com/en-us/azure/sentinel/connect-custom-logs?tabs=DCG https://docs.microsoft.com/en-us/azure/sentinel/roles
New Question 15:
You are designing security for an Azure landing zone.
Your company identifies the following compliance and privacy requirements:
1.
Encrypt cardholder data by using encryption keys managed by the company.
2.
Encrypt insurance claim files by using encryption keys hosted on-premises.
Which two configurations meet the compliance and privacy requirements? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Store the cardholder data in an Azure SQL database that is encrypted by using Microsoft-managed keys.
B. Store the insurance claim data in Azure Blob storage encrypted by using customer-provided keys.
C. Store the cardholder data in an Azure SQL database that is encrypted by using keys stored in Azure Key Vault Managed HSM.
D. Store the insurance claim data in Azure Files encrypted by using Azure Key Vault Managed HSM.
Correct Answer: BC
-C: Encrypt cardholder – “managed by company” but can be stored in Azure Key Vault Managed HSM, (BYOK)
-B: Encrypt insurance – “key hosted on-prem” – only customer-provided key is stored in customer store in on-prem, (HYOK). Take a look at the table under the link and read the article.
…
Conclusion
Microsoft SC-100 dumps: is the best solution for Microsoft Cybersecurity Architect! Using the latest and effective Microsoft Cybersecurity Architect Expert certification exam program can not only make you progress quickly but also help you pass the exam 100% successfully.
You can take advantage of the free Microsoft SC-100 dumps exam questions to help you validate your current learning and advance your expertise! Download 100% Best Microsoft Cybersecurity Architect Expert Certification Exam Scenario: Microsoft SC-100 dumps with PDF and VCE: https://www.leads4pass.com/sc-100.html Really helps you pass the exam 100% successfully!
Frequently Asked Questions
Can Microsoft SC-100 Dumps Really Pass the Exam Successfully?
Yes absolutely! This exam material completely covers the actual exam! It has been verified to be true and effective.
Will Microsoft Cybersecurity Architect SC-100 still be popular in 2025?
The Microsoft Cybersecurity Architect Expert (SC-100) certification, while a bit older, can still be a valuable asset in 2025, depending on your career goals and the specific cybersecurity landscape within your industry.
It is still important if your career direction is related to the following, for example:
- Identity and Access Management: Crucial in today’s hybrid work environment.
- Data Security: Protecting sensitive data remains a top priority for organizations.
- Threat Modeling and Risk Assessment: Essential skills for any cybersecurity professional.
- Security Architecture Principles: Foundational knowledge that can be applied across various security domains.
What is the salary level for the Microsoft Cyber Security Architect (SC-100) certification?
The Microsoft Cyber Security Architect (SC-100) certification can significantly impact your earning potential. Here is past data from the United States:
- Average Salary: $110,000 – $150,000 per year
- Top Earners: Can potentially earn upwards of $200,000 per year or more, depending on experience, skills, and location.
Disclaimer: The above data is calculated from the Internet, but it will not be very different from the actual situation. There are many factors that really affect your salary, such as experience, work location, company size, additional certifications, skills, and professional knowledge…
Discover more from Collect the latest Microsoft (Azure, Dynamics 365, Microsoft 365, Fundamentals, MTA...) exam questions and answers-Advanced sharing with Cisco, CompTIA, Citrix
Subscribe to get the latest posts sent to your email.

