[Dec 2020] Cisco 200-201 exam dumps and online practice questions are available from Leads4Pass
The latest updated Cisco 200-201 exam dumps and free 200-201 exam practice questions and answers! Latest updates from leads4pass Cisco 200-201 Dump PDF and 200-201 Dump VCE, leads4pass 200-201 exam questions updated and answers corrected! Get the full Cisco 200-201 dumps from leads4pass 200-201 (VCE&PDF)
Latest 200-201 PDF for free
Share the Cisco 200-201 Dumps PDF for free From leads4pass 200-201 Dumps part of the distraction collected on Google Drive shared by leads4pass
https://drive.google.com/file/d/1YbTC7VnpiP26Cp2XUgxInHTyiZdr1GGh/
Latest leads4pass 200-201 Youtube
Share the latest Cisco 200-201 exam practice questions and answers for free from Led4Pass Dumps viewed online by Youtube Videos
The latest updated Cisco 200-201 Exam Practice Questions and Answers Online Practice Test is free to share from leads4pass (Q1-Q13)
QUESTION 1
Which type of data collection requires the largest amount of storage space?
A. alert data
B. transaction data
C. session data
D. full packet capture
Correct Answer: D
QUESTION 2
What does cyber attribution identity in an investigation?
A. cause of an attack
B. exploit of an attack
C. vulnerabilities exploited
D. threat actors of an attack
Correct Answer: D
QUESTION 3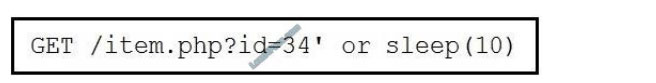
Refer to the exhibit. This request was sent to a web application server driven by a database.
Which type of web server attack is represented?
A. parameter manipulation
B. heap memory corruption
C. command injection
D. blind SQL injection
Correct Answer: D
QUESTION 4
What is the benefit of agent-based protection when compared to agentless protection?
A. It lowers maintenance costs
B. It provides a centralized platform
C. It collects and detects all traffic locally
D. It manages numerous devices simultaneously
Correct Answer: B
QUESTION 5
What is the difference between statistical detection and rule-based detection models?
A. Rule-based detection involves the collection of data in relation to the behavior of legitimate users over a period of
time
B. Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an
IF/THEN basis
C. Statistical detection involves the evaluation of an object on its intended actions before it executes that behavior
D. Rule-based detection defines legitimate data of users over a period of time and statistical detection defines it on an
IF/THEN basis
Correct Answer: B
QUESTION 6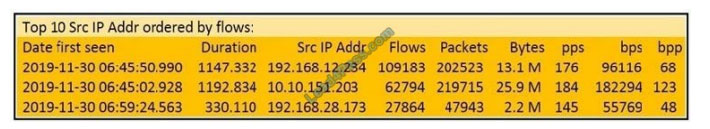
Refer to the exhibit. What information is depicted?
A. IIS data
B. NetFlow data
C. network discovery event
D. IPS event data
Correct Answer: B
QUESTION 7
How does an attacker observe network traffic exchanged between two users?
A. port scanning
B. man-in-the-middle
C. command injection
D. denial of service
Correct Answer: B
QUESTION 8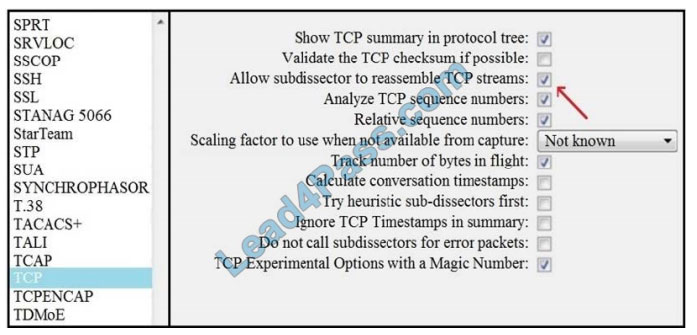
Refer to the exhibit. What is the expected result when the “Allow subdissector to reassemble TCP streams” feature is
enabled?
A. insert TCP subdissectors
B. extract a file from a packet capture
C. disable TCP streams
D. unfragment TCP
Correct Answer: D
QUESTION 9
What is the difference between inline traffic interrogation and traffic mirroring?
A. Inline inspection acts on the original traffic data flow
B. Traffic mirroring passes live traffic to a tool for blocking
C. Traffic mirroring inspects live traffic for analysis and mitigation
D. Inline traffic copies packets for analysis and security
Correct Answer: B
QUESTION 10
What causes events on a Windows system to show Event Code 4625 in the log messages?
A. The system detected an XSS attack
B. Someone is trying a brute force attack on the network
C. Another device is gaining root access to the system
D. A privileged user successfully logged into the system
Correct Answer: B
QUESTION 11
What makes HTTPS traffic difficult to monitor?
A. SSL interception
B. packet header size
C. signature detection time
D. encryption
Correct Answer: D
QUESTION 12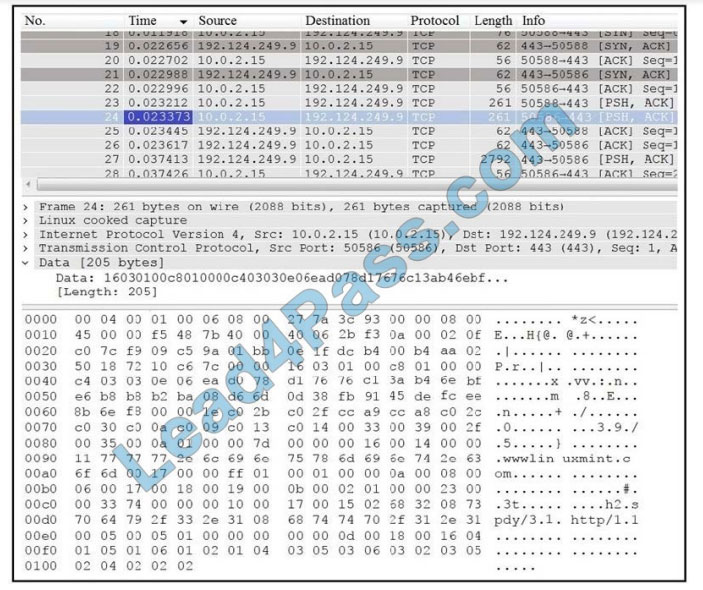
Refer to the exhibit. Which application protocol is in this PCAP file?
A. SSH
B. TCP
C. TLS
D. HTTP
Correct Answer: B
QUESTION 13
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its
integrity?
A. examination
B. investigation
C. collection
D. reporting
Correct Answer: C
Fulldumps shares the latest updated Cisco 200-201 exam exercise questions, 200-201 dumps pdf, and Youtube video learning for free.
All exam questions and answers come from the leads4pass exam dump shared part! leads4pass updates throughout the year and shares a portion of your exam questions for free to help you understand the exam content and enhance your exam experience!
Get the full Cisco 200-201 exam readiness dump questions at https://www.leads4pass.com/200-201.html (pdf&vce)
ps.
Get free Cisco 200-201 dumps PDF online: https://drive.google.com/file/d/1YbTC7VnpiP26Cp2XUgxInHTyiZdr1GGh/

