[Aug 2021] Microsoft 98-367 Exam Questions And Answers From Leads4pass | Latest Update

We share the latest updated Microsoft 98-367 test questions and answers for free, all test questions are real cracked, guaranteed to be true and effective! You can practice the test online! Or download the latest 98-367 exam pdf.
The free exam questions are only part of what we share. If you want to get the complete Microsoft 98-367 exam questions and answers, you can get them in leads4pass.
The leads4pass 98-367 exam dumps contain VCE dumps and PDF dumps.
Microsoft 98-367 Exam “Security Fundamentals” https://www.leads4pass.com/98-367.html (Total Questions: 277 Q&A)
Get FREE Microsoft 98-367 pdf from leads4pass for free
Free share Microsoft 98-367 exam PDF from Fulldumps provided by leads4pass
https://www.fulldumps.com/wp-content/uploads/2021/05/Lead4pass-Microsoft-MTA-98-367-Exam-Dumps-Braindumps-PDF-VCE.pdf
Microsoft 98-367 exam questions online practice test
QUESTION 1
You have a new computer and want to restrict other people from replacing the operating system.
Which action prevents a user from installing an alternate operating system by using physical media if the user has
physical media if the user has physical access to the computer?
A. installing drive-level encryption
B. disabling removable devices and drives
C. password protecting the computer BIOS
D. removing the user from the administrators group
Correct Answer: B
QUESTION 2
A Virtual Private Network (VPN) is a/an:
A. Intrusion Prevention System that filters unauthorized communications in the enterprise network
B. virtual communication method that stores data transmitted in a private environment
C. tunnel that prevents information that passes through it from being modified or stolen
D. perimeter network that contains secure virtual servers
Correct Answer: C
QUESTION 3
Which of the following is a mechanism that allows authentication of dial-in and other network connections?
A. VPN
B. NTFS
C. RADIUS
D. Single Sign-On
Correct Answer: C
RADIUS is a mechanism that allows authentication of dial-in and other network connections. RADIUS is a client/server
protocol that runs in the application layer, using UDP as transport. The Remote Access Server, the Virtual Private
Network server, the Network switch with port-based authentication, and the Network Access Server are all gateways
that control access to the network, and all have a RADIUS client component that communicates with the RADIUS
server. The RADIUS server is usually a background process running on a UNIX or Windows NT machine. RADIUS
serves three functions: To authenticate users or devices before granting them access to a network To authorize those
users or devices for certain network services To account for usage of those services Answer: D is incorrect. Single SignOn is an approach which involves a server that acts as an online certificate authority within a single sign-on system. A
single sign-on server will issue digital certificates into the client system, but never stores them. Users can execute
programs, etc. with the temporary certificate. It is common to find this solution variety with x.509-based certificates.
Answer: B is incorrect. NTFS is a high-performance file system proprietary to Microsoft. NTFS supports file-level
security, compression, and auditing. It also supports large volumes and powerful storage solution such as RAID. The
latest feature of NTFS is its ability to encrypt files and folders to protect sensitive data. Answer: A is incorrect. A virtual
private network (VPN) is a form of wide area network (WAN) that supplies network connectivity over a possibly long
physical distance. A virtual private network is a network that uses a public telecommunication infrastructure, such as the
Internet, to provide remote offices or individual users with secure access to their organization\\’s network. A virtual
private network can be contrasted with an expensive system of owned or leased lines that can only be used by one
organization. The goal of a VPN is to provide the organization with the same capabilities, but at a much lower cost. A
VPN works by using the shared public infrastructure while maintaining privacy through security procedures and
tunneling protocols such as the Layer Two Tunneling Protocol (L2TP). In effect, the protocols, by encrypting data at the
sending end and decrypting it at the receiving end, send the data through a tunnel that cannot be entered by data that is
not properly encrypted. An additional level of security involves encrypting not only the data, but also the originating and
receiving network addresses.
QUESTION 4
Which of the following contains a tree of domain names?
A. Domain name space
B. Domain name formulation
C. Domain Name System
D. Authoritative name server
Correct Answer: A
Domain name space consists of a tree of domain names. Each node or leaf in the tree has zero or more resource
records, which hold information associated with the domain name. The tree sub- divides into zones starting at the root
zone.
Answer: B is incorrect. The definitive descriptions of the rules for forming domain names appear in RFC 1035, RFC
1123, and RFC 2181. A domain name consists of one or more parts, technically called labels that are conventionally
concatenated, and delimited by dots.
Answer: C is incorrect. Domain Name System (DNS) is a distributed hierarchical naming system for computers,
services, or other resources connected to the Internet or a private network. It associates various information with
domain names
assigned to each of the participants.
Answer: D is incorrect. An authoritative name server is a name server that gives answers that have been configured by
an original source, for example, the domain administrator or by dynamic DNS methods, in contrast to the answers that
were obtained via a regular DNS query to one more name server. An authoritative-only name server only returns
answers to the queries about domain names that have been specifically configured by the administrator.
QUESTION 5
Which of the following viruses cannot be detected by the signature-based antivirus?
A. Polymorphic
B. MBR virus
C. Boot sector
D. Macro
Correct Answer: A
A polymorphic virus has the ability to change its own signature at the time of infection. This virus is very complicated
and hard to detect. When the user runs the infected file in the disk, it loads the virus into the RAM. The new virus starts
making its own copies and infects other files of the operating system. The mutation engine of the polymorphic virus
generates a new encrypted code, thus changing the signature of the virus. Therefore, polymorphic viruses cannot be
detected by signature-based antivirus. Answer: B is incorrect. A Master boot record (MBR) virus replaces the boot
sector data with its own malicious code. Every time when the computer starts up, the boot sector virus executes. It can
then generate activity that is either annoying (system will play sounds at certain times) or destructive (erase the hard
drive of the system). Because the code in the Master Boot Record executes before any operating system is started, no
operating system can detect or recover from corruption of the Master Boot Record.
Answer: D is incorrect. A macro virus is a virus that consists of a macro code which infects the system. A Macro virus
can infect a system rapidly. Since this virus has VB event handlers, it is dynamic in nature and displays random
activation. The victim has only to open a file having a macro virus in order to infect the system with the virus. DMV,
Nuclear, and Word Concept are some good examples of macro viruses. Answer: C is incorrect. A boot sector virus
infects the master boot files of the hard disk or floppy disk. Boot record programs are responsible for booting the
operating system and the boot sector virus copies these programs into another part of the hard disk or overwrites these
files. Therefore, when the floppy or the hard disk boots, the virus infects the computer.
QUESTION 6
Which of the following is a tool that can be used to evaluate the servers having vulnerabilities that are related to the
operating system and installed software?
A. DNS dynamic update
B. Windows Software Update Services
C. Read-Only domain controller (RODC)
D. Microsoft Baseline Security Analyzer
Correct Answer: D
Microsoft Baseline Security Analyzer is a tool that can be used to evaluate the servers having vulnerabilities that are
related to the operating system and installed software Microsoft Baseline Security Analyzer (MBSA) is a software tool of
Microsoft to determine security state by assessing missing security updates and less- secure security settings within
Microsoft Windows, Windows components such as Internet Explorer, IIS web server, and products Microsoft SQL
Server,
and Microsoft Office macro settings. Microsoft Baseline Security Analyzer (MBSA) includes a graphical and command
line interface that can perform local or remote scans of Windows systems.
Answer: B is incorrect. Windows Server Update Services (WSUS) is an add- on component of Windows Server 2008. It
provides functionality to a server to run as a Windows Update server in a Windows network environment.
Administrators
can configure a WSUS server as the only server to download updates from Windows site, and configure other
computers on the network to use the server as the source of update files. This will save lots of bandwidth as each
computer will not
download updates individually. WSUS 3.0 SP1 is the only version of WSUS that can be installed on Windows Server
2008. Earlier versions of WSUS cannot be installed on a server running Windows Server 2008.
Answer: C is incorrect. Read-only Domain Controller (RODC) is a domain controller that hosts the read-only partition of
the Active Directory database. RODC was developed by Microsoft typically to be deployed in a branch office
environment.
RODC is a good option to enhance security by placing it in a location where physical security is poor. RODC can also
be placed at locations having relatively few users and a poor network bandwidth to the main site. As only the read-only
partition of the Active Directory database is hosted by RODC, a little local IT knowledge is required to maintain it.
Answer: A is incorrect. DNS dynamic update is used to enable DNS client computers for registering and dynamically
updating their resource records with a DNS server whenever any modification or change has been taken place. It is
used to
update the DNS client computers with the reflecting changes.
QUESTION 7
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network. You plan to
connect your company\\’s LAN to the Internet. You are concerned about the security of your network and want to protect
it against external access and misuse. Which device will you install between your LAN and the Internet to accomplish
this?
Select and Place: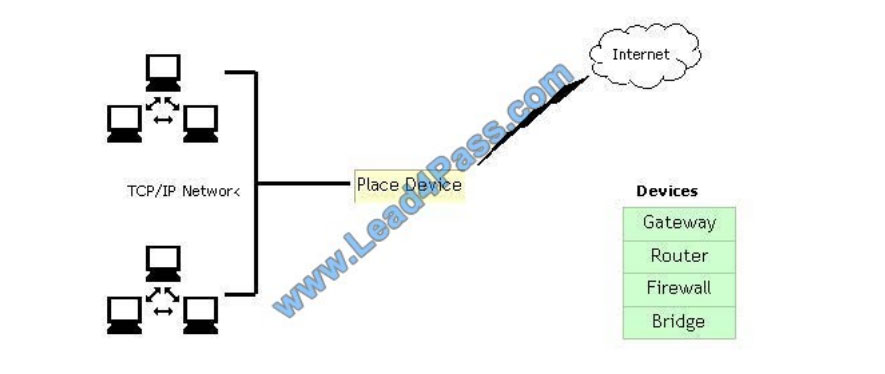
Correct Answer:
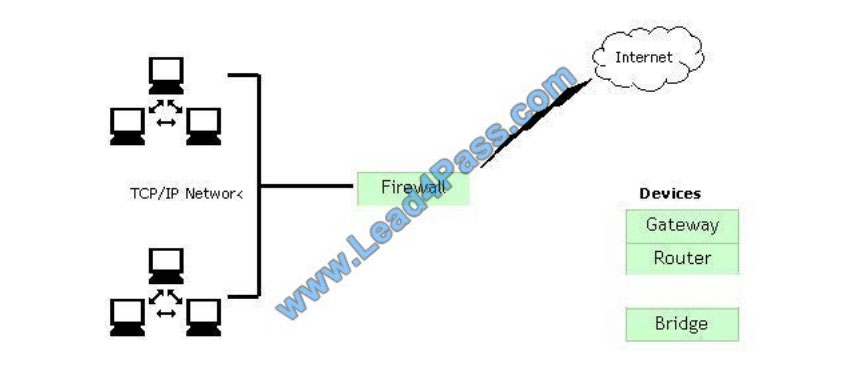
QUESTION 8
What are three examples of factors required for multi-factor authentication? (Choose three.)
A. a username
B. a smart card
C. a fingerprint
D. a password challenge question
E. a pin number
Correct Answer: ACE
References: https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-methods
QUESTION 9
Physically securing servers prevents:
A. Theft
B. Compromise of the certificate chain
C. Man-in-the middle attacks
D. Denial of Service attacks
Correct Answer: A
QUESTION 10
Which of the following actions should be taken so that the computer requires confirmation before installing an ActiveX
component?
A. Configuring a firewall on the network
B. Configuring the settings on the Web Browser
C. Installing an anti-virus software
D. Configuring DMZ on the network
Correct Answer: B
Configuring the settings on the Web browser will enable a computer to ask for confirmation before installing an ActiveX
component. This will enable users to prevent the download of potentially unsafe controls onto the computer. ActiveX
controls are software components that can be integrated into Web pages and applications, within a computer or among
computers in a network, to reuse the functionality. Reusability of controls reduces development time of applications and
improves program interfaces.
They enhance the Web pages with formatting features and animation. ActiveX controls can be used in applications
written in different programming languages that recognize Microsoft\\’s Component Object Model (COM). These
controls
always run in a container. ActiveX controls simplify and automate the authoring tasks, display data, and add functionality
to Web pages.
Answer: A and D are incorrect. Configuring a firewall or DMZ will not help in accomplishing the task.
QUESTION 11
Which of the following is a set of rules that control the working environment of user accounts and computer accounts?
A. Mandatory Access Control
B. Access control list
C. Group Policy
D. Intrusion detection system
Correct Answer: C
Group Policy is a feature of the Microsoft Windows NT family of operating systems. It is a set of rules, which control the
working environment of user accounts and computer accounts. Group Policy provides the centralized management and
configuration of operating systems, applications, and users\\’ settings in an Active Directory environment. Group Policy
is often used to restrict certain actions that may pose potential security risks. For example, block access to the Task
Manager, restrict access to certain folders, disable the downloading of executable files, and so on. As part of
Microsoft\\’s IntelliMirror technologies, Group Policy aims to reduce the cost of supporting users. IntelliMirror
technologies relate to the management of disconnected machines or roaming users and include roaming user profiles,
folde redirection, and offline files.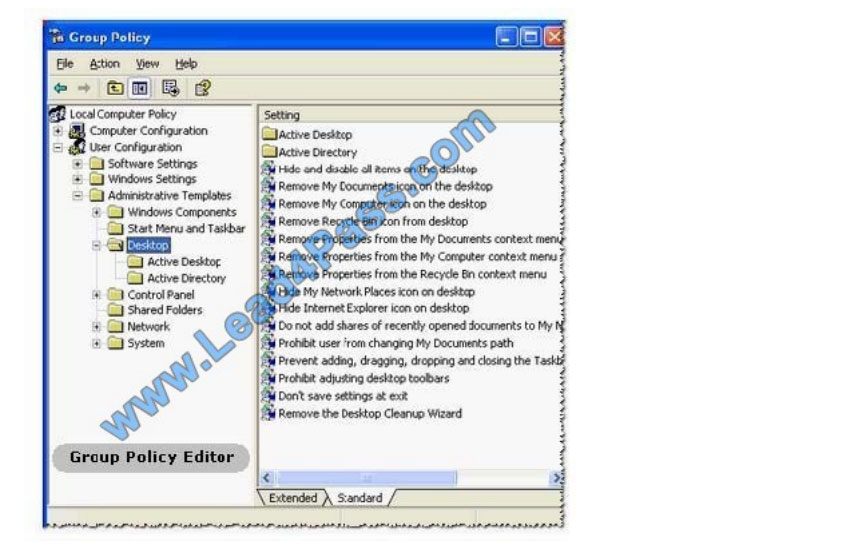
Answer: A is incorrect. Mandatory Access Control (MAC) is a model that uses a predefined set of access privileges for
an object of the system. Access to an object is restricted on the basis of the sensitivity of the object and granted through
authorization. Sensitivity of an object is defined by the label assigned to it. For example, if a user receives a copy of an
object that is marked as “secret”, he cannot grant permission to other users to see this object unless they have the
appropriate permission. Answer: D is incorrect. An Intrusion detection system (IDS) is used to detect unauthorized
attempts to access and manipulate computer systems locally or through the Internet or an intranet. It can detect several
types of attacks and malicious behaviors that can compromise the security of a network and computers. This includes
network attacks against vulnerable services, unauthorized logins, and access to sensitive data, and malware (e.g.
viruses, worms, etc.). An IDS also detects attacks that originate from within a system. In most cases, an IDS has three
main components: Sensors, Console, and Engine. Sensors generate security events. A console is used to alert and
control sensors and to monitor events. An engine is used to record events and to generate security alerts based on
received security events. In many IDS implementations, these three components are combined into a single device.
Basically, the following two types of IDS are used: Network-based IDS Host-based IDS Answer: B is incorrect. Access
control list (ACL) is a rule list containing access control entries. It is used to allow or deny access to network resources.
ACL can be implemented on network users and network devices such as routers and firewalls. Routers and firewalls
use ACL to determine which packets should be forwarded or dropped.
QUESTION 12
Humongous Insurance needs to set up a domain controller in a branch office. Unfortunately, the server cannot be
sufficiently secured from access by employees in that office, so the company is installing a Primary Domain Controller.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if
the underlined text makes the statement correct.
A. Read-Only Domain Controller
B. Backup Domain Controller
C. Active Directory Server
D. No change is needed.
Correct Answer: A
QUESTION 13
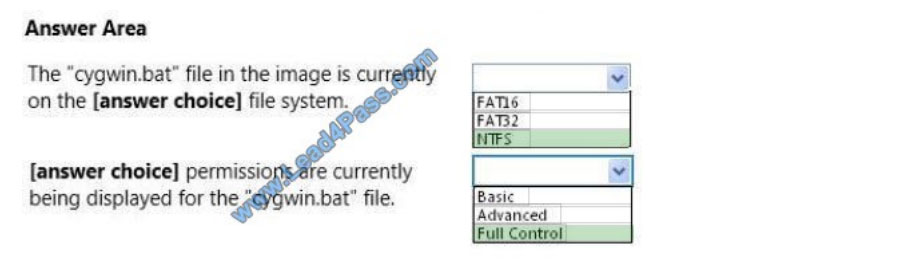
Your supervisor asks you to review file permission settings on the application.bat file. You need to report which file
system the file is on and the type of permission the file has. You review the application Properties dialog box shown in
the following image:
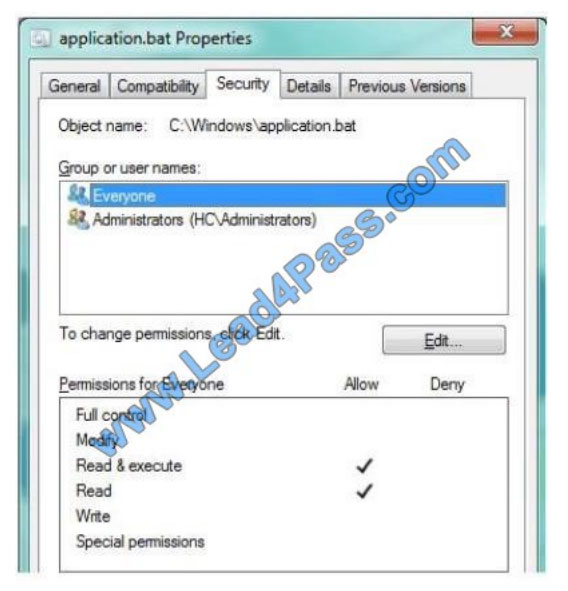
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth
one point.
Hot Area:
Correct Answer:
Thank you for reading! I have told you how to successfully pass the Microsoft 98-367 exam.
You can choose: https://www.leads4pass.com/98-367.html to directly enter the 98-367 Exam dumps channel! Get the key to successfully pass the exam!
Wish you happiness!
Get free Microsoft 98-367 exam PDF online: https://www.fulldumps.com/wp-content/uploads/2021/05/Lead4pass-Microsoft-MTA-98-367-Exam-Dumps-Braindumps-PDF-VCE.pdf

