Microsoft Azure Security Technologies AZ-500 Dumps Update [2022]
Microsoft AZ-500 dumps have been updated for the 2022 Microsoft Azure Security Technologies Certification Exam Prep.
leads4pass AZ-500 dumps material is updated with 364 new practice questions and answers based on the following core knowledge: Implementing Azure security controls that protect identity, access, data, applications, and networks in cloud and hybrid environments as part of an end-to-end infrastructure.
Therefore, you just need to follow these steps to help you successfully pass the Microsoft Azure Security Technologies AZ-500 exam:
- Download AZ-500 dumps: https://www.leads4pass.com/az-500.html
- Complete all AZ-500 Dumps practice exercises
- Prepare for 165$ to take the exam
- You have to remember to complete 40 to 60 questions in 150-210 minutes (One lab with around 12 sub-tasks)
- Waiting for the result after the exam
- Congratulations on successfully passing the Microsoft Azure Security Technologies AZ-500 exam
It’s that simple, you can test some of the AZ-500 dumps exam questions online:
Verification results at the end of the article
QUESTION 1:
You are troubleshooting a security issue for an Azure Storage account.
You enable the diagnostic logs for the storage account.
What should you use to retrieve the diagnostics logs?
A. Azure Storage Explorer
B. SQL query editor in Azure
C. File Explorer in Windows
D. Azure Security Center
QUESTION 2:
You have an Azure subscription that contains virtual machines.
You enable just-in-time (JIT) VM access to all the virtual machines.
You need to connect to a virtual machine by using Remote Desktop.
What should you do first?
A. From Azure Directory (Azure AD) Privileged Identity Management (PIM), activate the Security administrator user role.
B. From Azure Active Directory (Azure AD) Privileged Identity Management (PIM), activate the Owner role for the virtual machine.
C. From the Azure portal, select the virtual machine, select Connect, and then select Request access.
D. From the Azure portal, select the virtual machine and add the Network Watcher Agent virtual machine extension.
QUESTION 3:
HOTSPOT
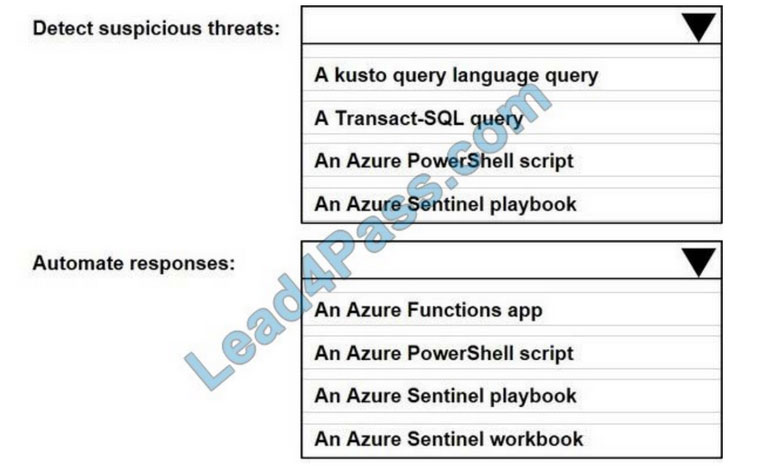
You plan to use Azure Sentinel to create an analytic rule that will detect suspicious threats and automate responses.
Which components are required for the rule? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
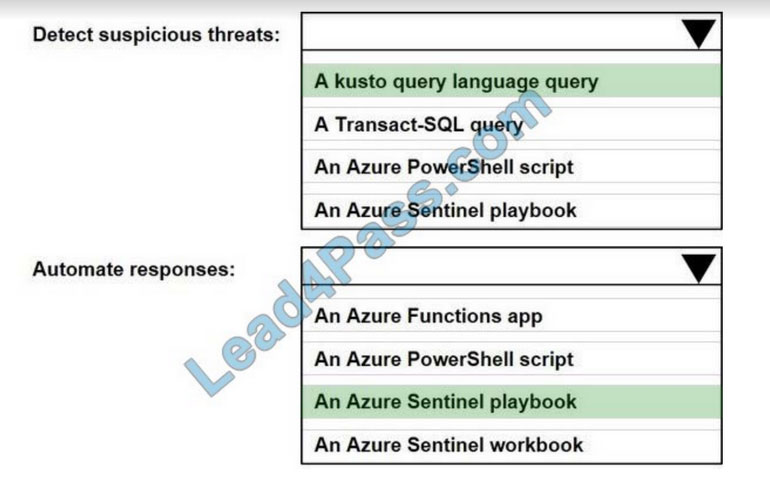
Reference: https://docs.microsoft.com/en-us/azure/sentinel/tutorial-detect-threats-custom https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
QUESTION 4:
Your company has an Azure subscription named Sub1 that is associated to an Azure Active Directory Azure (Azure AD) tenant named contoso.com.
The company develops a mobile application named App1. App1 uses the OAuth 2 implicit grant type to acquire Azure AD access tokens.
You need to register App1 in Azure AD.
What information should you obtain from the developer to register the application?
A. a redirect URI
B. a reply URL
C. a key
D. an application ID
QUESTION 5:
SIMULATION
You need to configure a weekly backup of an Azure SQL database named Homepage. The backup must be retained for eight weeks.
To complete this task, sign in to the Azure portal.
A. See the below.
QUESTION 6:
SIMULATION
You need to ensure that only devices connected to a 131.107.0.0/16 subnet can access data in the rg1lod10598168 Azure Storage account.
To complete this task, sign in to the Azure portal.
A. See the below.
QUESTION 7:
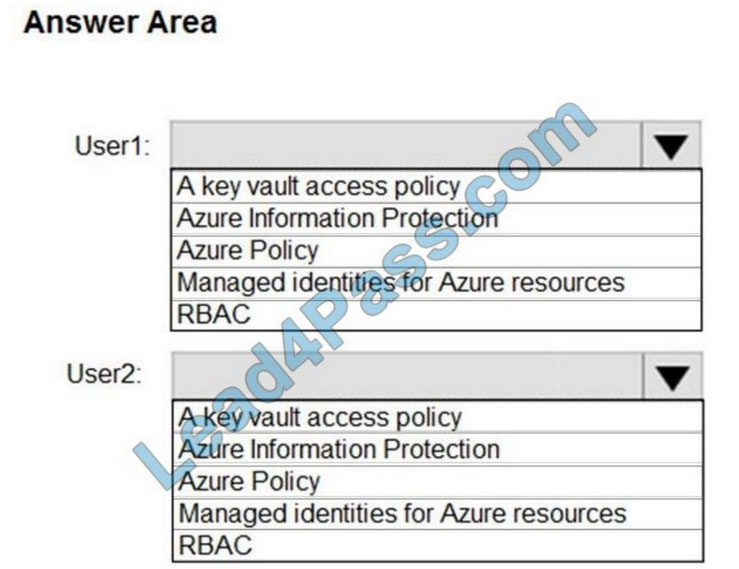
You have an Azure key vault.
You need to delegate administrative access to the key vault to meet the following requirements:
1.
Provide a user named User1 with the ability to set advanced access policies for the key vault.
2.
Provide a user named User2 with the ability to add and delete certificates in the key vault.
3.
Use the principle of least privilege.
What should you use to assign access to each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
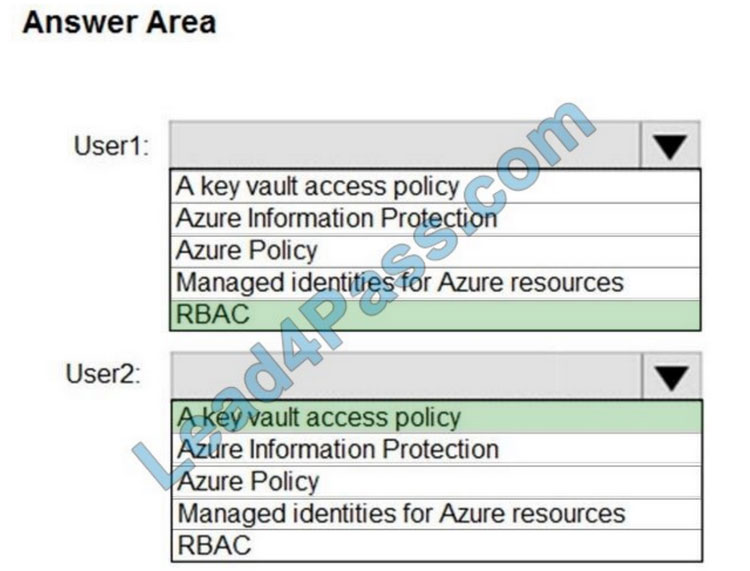
User1: RBAC
RBAC is used as the Key Vault access control mechanism for the management plane. It would allow a user with the proper identity to:
1.
set Key Vault access policies
2.
create, read, update, and delete key vaults
3.
set Key Vault tags
Note: Role-based access control (RBAC) is a system that provides fine-grained access management of Azure resources. Using RBAC, you can segregate duties within your team and grant only the amount of access to users that they need to perform their jobs.
User2: A key vault access policy
A key vault access policy is the access control mechanism to get access to the key vault data plane. Key Vault access policies grant permissions separately to keys, secrets, and certificates.
References: https://docs.microsoft.com/en-us/azure/key-vault/key-vault-secure-your-key-vault
QUESTION 8:
You have Azure virtual machines that have Update Management enabled. The virtual machines are configured as shown in the following table.
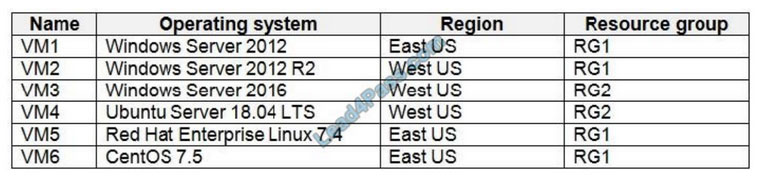
You schedule two update deployments named Update1 and Update2. Update1 updates VM3. Update2 updates VM6.
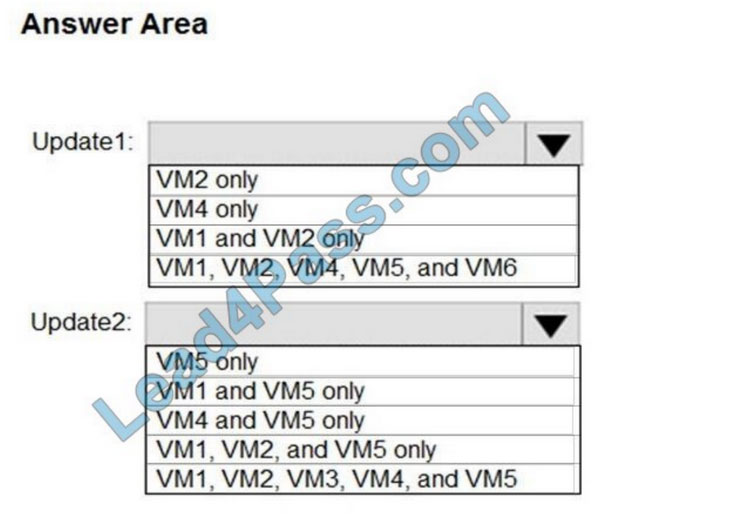
Which additional virtual machines can be updated by using Update1 and Update2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
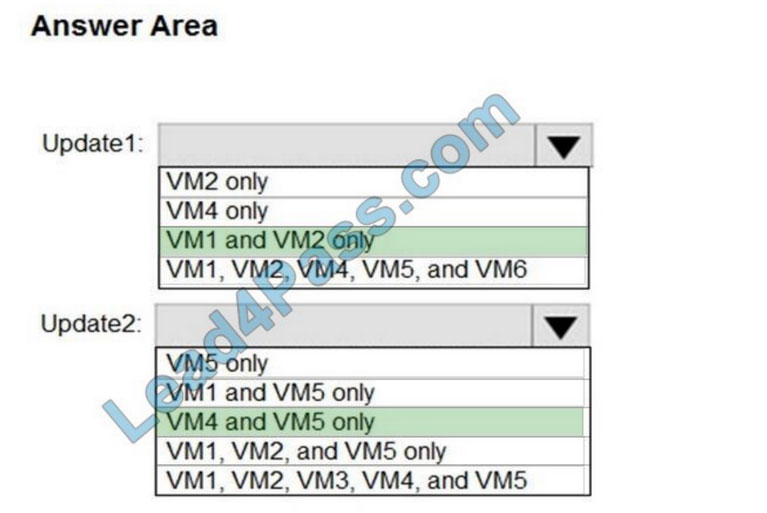
Update1: VM1 and VM2 only VM3: Windows Server 2016 West US RG2
Update2: VM4 and VM5 only VM6: CentOS 7.5 East US RG1
For Linux, the machine must have access to an update repository. The update repository can be private or public.
References: https://docs.microsoft.com/en-us/azure/automation/automation-update-management
QUESTION 9:
You have an Azure subscription that contains a resource group named RG1 and a security group serverless RG1 contains 10 virtual machines, a virtual network VNET1, and a network security group (NSG) named NSG1. ServerAdmins can access the virtual machines by using RDP. You need to ensure that NSG1 only RDP connections to the virtual for a maximum of 60 minutes when a member of ServerAdmins requests access.
What should you configure?
A. an Azure Active Directory (Azure AD) Privileged Identity Management (PIM) role assignment.
B. a just in time (JIT) VM access policy in Azure Security Center
C. an azure policy assigned to RG1.
D. an Azure Bastion host on VNET1.
QUESTION 10:
You have an Azure subscription.
You create an Azure web app named Contoso1812 that uses an S1 App service plan.
You create a DNS record for www.contoso.com that points to the IP address of Contoso1812.
You need to ensure that users can access Contoso1812 by using the https://www.contoso.com URL.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Turn on the system-assigned managed identity for Contoso1812.
B. Add a hostname to Contoso1812.
C. Scale-out the App Service plan of Contoso1812.
D. Add a deployment slot to Contoso1812.
E. Upload a PFX file to Contoso1812
QUESTION 11:
You have an Azure subscription that contains an Azure Active Directory (Azure AD) tenant and a user named User1.
The App registration settings for the tenant are configured as shown in the following exhibit.

You plan to deploy an app named App1.
You need to ensure that User1 can register App1 in Azure AD. The solution must use the principle of least privilege.
Which role should you assign to User1?
A. App Configuration Data Owner for the subscription
B. Managed Application Contributor for the subscription
C. Cloud application administrator in Azure AD
D. Application developer in Azure AD.
QUESTION 12:
HOTSPOT
Your network contains an on-premises Active Directory domain that syncs to an Azure Active Directory (Azure AD) tenant. The tenant contains the users shown in the following table.
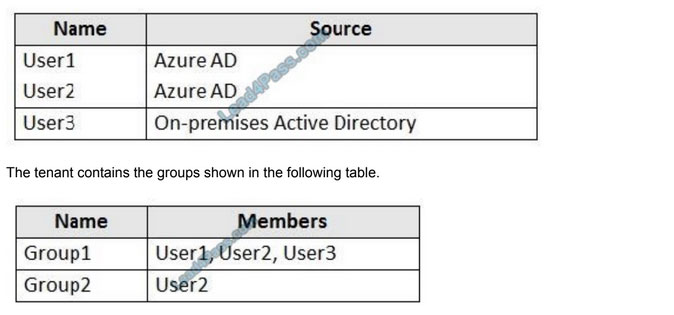
You configure the multi-factor authentication (MFA) registration policy and the following settings:
Assignments:
-Include: Group1
-Exclude Group2 Controls: Require Azure MFA registration Enforce Policy: On
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Hot Area:

Correct Answer:

QUESTION 13:
HOTSPOT
You need to ensure that the Azure AD application registration and consent configurations meet the identity and access requirements.
What should you use in the Azure portal? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
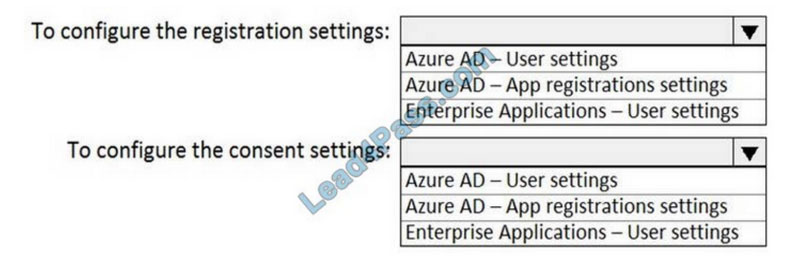
Correct Answer:
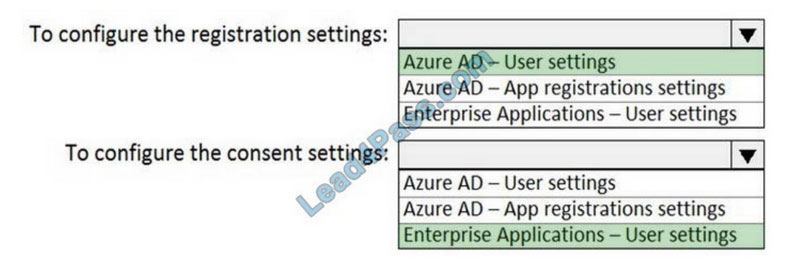
Reference: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/configure-user-consent
Validation results:
| Number: | Answers: | Explain: |
| Q1 | A | If you want to download the metrics for long-term storage or to analyze them locally, you must use a tool or write some code to read the tables. You must download the minute metrics for analysis. The tables do not appear if you list all the tables in your storage account, but you can access them directly by name. Many storage-browsing tools are aware of these tables and enable you to view them directly (see Azure Storage Client Tools for a list of available tools). Microsoft provides several graphical user interface (GUI) tools for working with the data in your Azure Storage account. All of the tools outlined in the following table are free. Note: There are several versions of this question in the exam. The questions in the exam have two different correct answers: 1. Azure Storage Explorer 2. AZCopy Other incorrect answer options you may see on the exam include the following: 1. Azure Monitor 2. The Security and Compliance admin center 3. Azure Cosmos DB explorer 4. Azure Monitor |
| Q2 | C | |
| Q3 | IMAGE | |
| Q4 | A | For Native Applications, you need to provide a Redirect URI, which Azure AD will use to return token responses. |
| Q5 | A | You need to configure the backup policy for the Azure SQL database. 1. In the Azure portal, type Azure SQL Database in the search box, select Azure SQL Database from the search results then select Homepage. Alternatively, browse to Azure SQL Database in the left navigation pane. 2. Select the server hosting the Homepage database and click on Manage backups. 3. Click on Configure policies. 4. Ensure that the Weekly Backups option is ticked. 5. Configure the How long would you like weekly backups to be retained the option to 8 weeks. 6. Click Apply to save the changes. |
| Q6 | A | Step 1: 1. In the Azure portal go to the storage account you want to secure. Here: rg1lod10598168 2. Click on the settings menu called Firewalls and virtual networks. 3. To deny access by default, choose to allow access from Selected networks. To allow traffic from all networks, choose to allow access from All networks. 4. Click Save to apply your changes. Step 2: 1. Go to the storage account you want to secure. Here: rg1lod10598168 2. Click on the settings menu called Firewalls and virtual networks. 3. Check that you\’ve selected to allow access from Selected networks. 4. To grant access to a virtual network with a new network rule, under Virtual networks, click Add an existing virtual network, select Virtual networks and Subnets options. Enter the 131.107.0.0/16 subnet and then click Add. Note: When network rules are configured, only applications requesting data over the specified set of networks can access a storage account. You can limit access to your storage account to requests originating from specified IP addresses, IP ranges, or from a list of subnets in an Azure Virtual Network (VNet). |
| Q7 | IMAGE | |
| Q8 | IMAGE | |
| Q9 | A | |
| Q10 | BE | B: You can configure Azure DNS to host a custom domain for your web apps. For example, you can create an Azure web app and have your users access it using either www.contoso.com or contoso.com as a fully qualified domain name (FQDN). To do this, you have to create three records: A root “A” record pointing to contoso.com A root “TXT” record for verification A “CNAME” record for the www name that points to the A record F: To use HTTPS, you need to upload a PFX file to the Azure Web App. The PFX file will contain the SSL certificate required for HTTPS. |
| Q11 | D | |
| Q12 | IMAGE | |
| Q13 | IMAGE |
[Google Drive] Download the above AZ-500 Dumps exam questions:https://drive.google.com/file/d/1OiSzSoI7GRtwMYVhNMqBpetd_mt73YYl/
Above I have told the steps to pass the Microsoft Azure Security Technologies AZ-500 exam, you can also click here to download the complete AZ-500 dumps exam questions.
Discover more from Collect the latest Microsoft (Azure, Dynamics 365, Microsoft 365, Fundamentals, MTA...) exam questions and answers-Advanced sharing with Cisco, CompTIA, Citrix
Subscribe to get the latest posts sent to your email.

